Microsoft has a free product named Local Administrator Password Solution (LAPS). This provides a centralized storage of local account passwords of domain joined computers in Active Directory. Domain Administrators can determine which users or groups are authorized to read the passwords using the LAPS User Interface (UI) or Powershell. Password complexity and expiration can be configured using Group Policy. When the local administrator password has expired, it is changed automatically and updated in Active Directory.
Use this instruction to implement Microsoft LAPS in your environment.
Install the software
First download the software. You can find the latest version here.
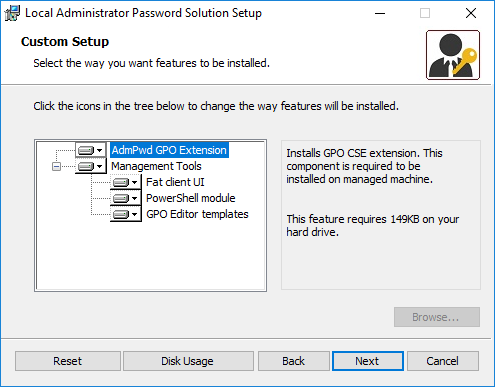
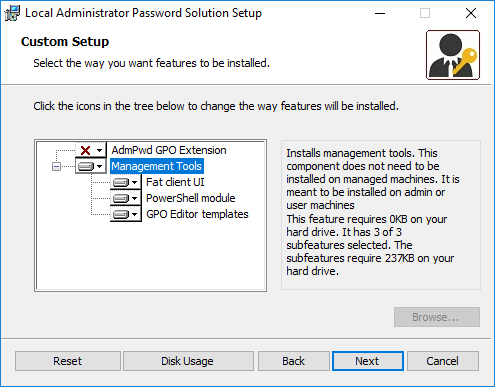
Install LAPS.x64.msi or LAPS.x86.msi on a Management Server of Management Workstation. If you install the msi on a Management Server or Workstation that needs to have its local account password stored in AD, you need to install the Group Policy Client Side Extension (CSE) Agent as well.
Install on Management Server/Workstation with Group Policy Client Side Extension (CSE) Agent
Install on Management Server/Workstation without Group Policy Client Side Extension (CSE) Agent
Extend the Active Directory Schema
The Active Directory Schema needs to be extended by two new attributes.
ms-Mcs-AdmPwd – Stores the password in clear text.
ms-Mcs-AdmPwdExpirationTime – Stores the expiration time of the password.
To extend the AD Schema, open a Powershell window on the Management Server/Workstation where the LAPS software has been installed. One of the components is the LAPS Powershell module. The logged on user account must be a member of the Schema Admins security group.
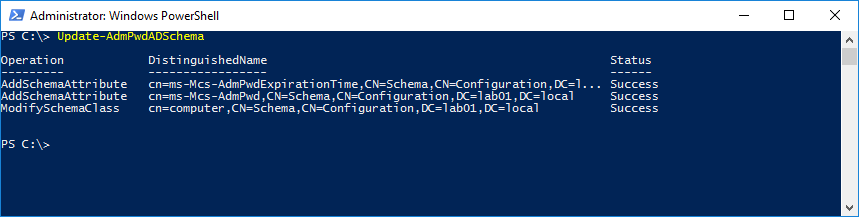
Use the Update-AdmPwdADSchema cmdlet to extend the AD Schema:
Update-AdmPwdADSchema
The result should be:
Set the permission for computers to update their password
To allow a computer to update its password attribute, use the Set-AdmPwdComputerSelfPermission cmdlet. You need to use this cmdlet for every organizational unit (OU) that contains computers that need to rotate their local account’s password. You can use the OU’s Canonical Name (CN) or the Distinguished Name (DN). Use the DN if the CN is not unique.
Example:
Set-AdmPwdComputerSelfPermission -OrgUnit "OU=Servers,OU=Computers,OU=Org,DC=lab01,DC=local"
or
Set-AdmPwdComputerSelfPermission -OrgUnit "Servers"
Configure Extended Rights for LAPS Groups of Users
First, find users or groups that already have extended rights to read the password. To find the extended right, use the Find-AdmPwdExtendedrights cmdlet.
Example:
Find-AdmPwdExtendedrights -identity "OU=Servers,OU=Computers,OU=Org,DC=lab01,DC=local"
or
Find-AdmPwdExtendedrights -identity "Servers"
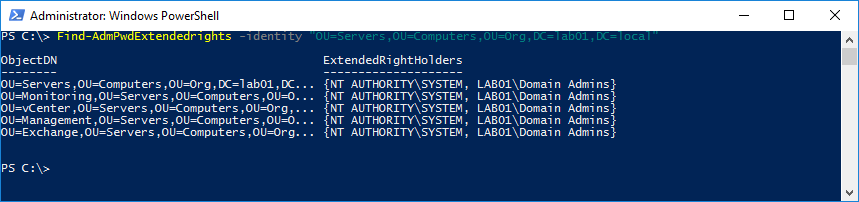
If the result is like this, there are no non-default users or groups that have extended rights on the specific OU or its child OUs. If a specific user or group has extended rights that need to be removed, use ADSIEdit to remove the extended rights.
Open ADSIEdit and connect to Default naming context. Browse to the specific OU and open its properties. Click on the Security tab and click on Advanced. Select the user or group and click on Edit. Uncheck all extended rights.
Now check the extended rights using the Find-AdmPwdExtendedrights cmdlet again to see if the removal was successful.
To grant specific users or groups extended rights to read the password, use the Set-AdmPwdReadPasswordPermission cmdlet.
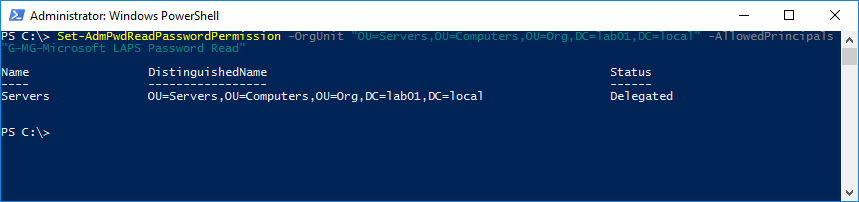
In this example, the group “G-MG-Microsoft LAPS Password Read” is granted Read Password Permission:
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=Servers,OU=Computers,OU=Org,DC=lab01,DC=local" -AllowedPrincipals "G-MG-Microsoft LAPS Password Read"
or
Set-AdmPwdReadPasswordPermission -OrgUnit "Servers" -AllowedPrincipals "G-MG-Microsoft LAPS Password Read"
To check if the configuration was successful, use the Find-AdmPwdExtendedrights cmdlet again.
Example:
Find-AdmPwdExtendedrights -identity "OU=Servers,OU=Computers,OU=Org,DC=lab01,DC=local"
or
Find-AdmPwdExtendedrights -identity "Servers"
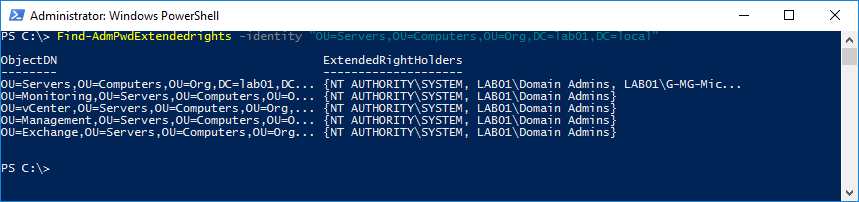
The result shows that the “G-MG-Microsoft LAPS Password Read” group has been granted the Read Password Permission extended right on the specific OU.
Repeat this for other users or groups on this or other OUs if required.
Enable LAPS using Group Policy
To enable LAPS for computers in an OU, create a GPO for that OU or edit an existing GPO. To be able to configure the LAPS settings, use the AdmPwd.admx and AdmPwd.adml files in the local PolicyDefinitions folder on the Management Server or Workstation where LAPS was installed (usually C:\Windows\PolicyDefinitions). If a central store is used, copy the files to your central store (\\<domain fqdn>\SYSVOL\<domain fqdn>\Policies\PolicyDefinitions).
Open the Group Policy Management Console (GPMC) and browse to the specific OU to create a new GPO or edit an existing one.
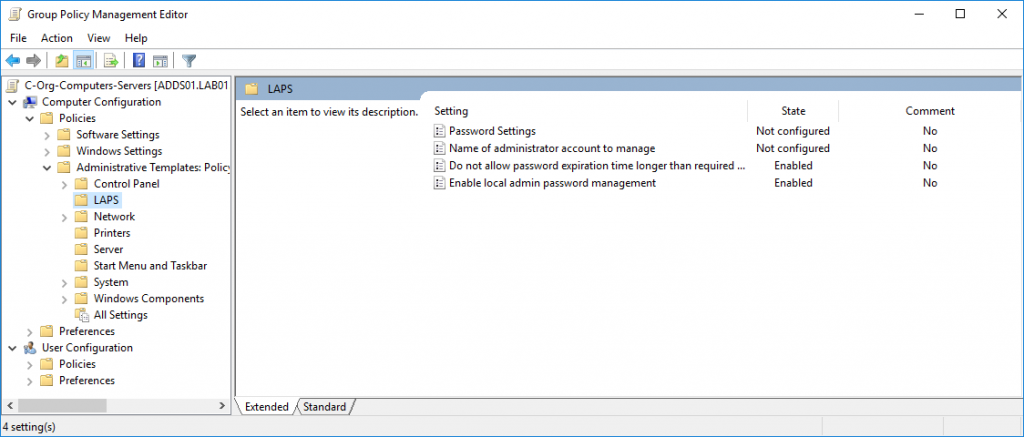
Enable the setting “Enable local admin password management”.
Optionally, configure one of the other settings. In this example the setting “Do not allow password expiration time longer than required by policy” has been enabled. When you enable this setting, planned password expiration longer than password age dictated by “Password Settings” policy is NOT allowed. When such expiration is detected, the password is changed immediately and password expiration is set according to policy.
By default, the password complexity is “Large letters + small letters + numbers + specials”, Password Length is 14 characters and Password Age is 30 days. To change this, enable the “Password Settings” setting and change one or more of the settings.
To specify the name of the local administrator account, enable the “Name of administrator account to manage” setting and specify the name of the administrator account. DO NOT configure this when the built-in admin account is used. The built-in admin account is auto-detected by well-known SID, even when renamed. DO configure when a custom local admin account is used.
Deploy the LAPS agent to all required computers
To deploy the LAPS agent, install the agent on all required computers manually, or use a distribution method like Group Policy or System Center Configuration Manager.
Install at least the AdmPwd GPO Extension.
To install the x64 agent using commandline, use:
msiexec /i "LAPS.x64.msi" /q
To install the x86 agent using commandline, use:
msiexec /i "LAPS.x86.msi" /q
Read a local account password from Active Directory
To read a local account password from Active Directory, logon to a Management Server of Workstation using an account that is member of the Domain Admins group or a specific group that has been granted the Read Password Permission extended right.
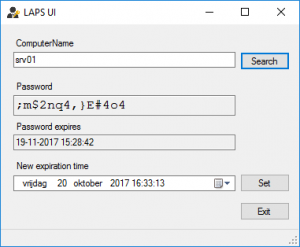
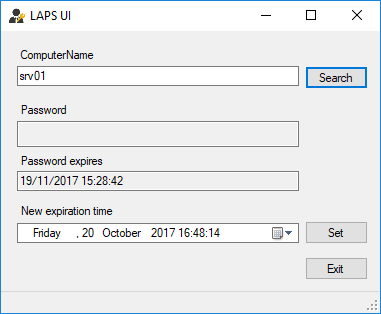
Open the LAPS UI, fill in the ComputerName field and click Search. A password should be visible in the Password field.
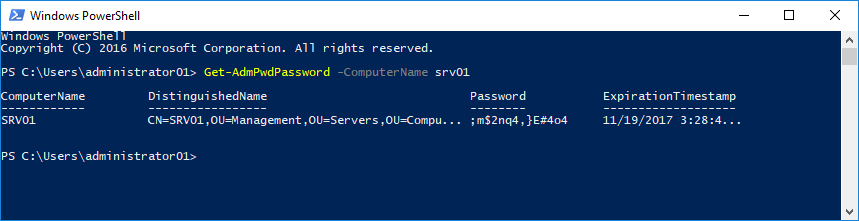
To use Powershell to show the local administrator account password of a specific computer, use the Get-AdmPwdPassword cmdlet.
Example:
Get-AdmPwdPassword -Computername srv01
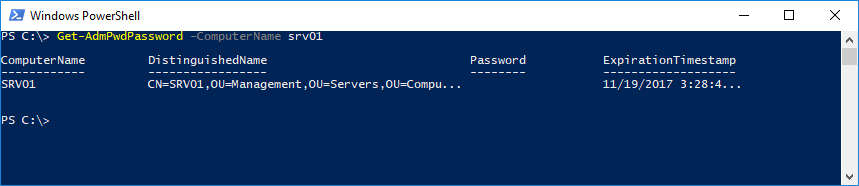
If you are not a member of the Domain Admins group or a specific group that has been granted the Read Password Permission extended right, the Password field is empty but you can still see the Expiration Time.
Final
Microsoft LAPS is a nice solution to cope with local administrator account passwords. I hope this article will help you setup LAPS in your environment.
Please let me know if you have any questions about this article.


LAPS rocks !!!. Nice post Johan. Greets Marc